本文最后更新于:2025年2月4日 下午
PNG图片隐写改高宽的反CRC
1
2
3
4
5
6
7
8
9
10
11
12
13
| import os
import binascii
import struct
crcbp = open("C:\\Users\\Smartisan\\Desktop\\e1.png", "rb").read()
for i in range(2000):
for j in range(2000):
data = crcbp[12:16] + \
struct.pack('>i', i)+struct.pack('>i', j)+crcbp[24:29]
crc32 = binascii.crc32(data) & 0xffffffff
if(crc32 == 0xa8586b45):
print(i, j)
print('hex:', hex(i), hex(j))
|
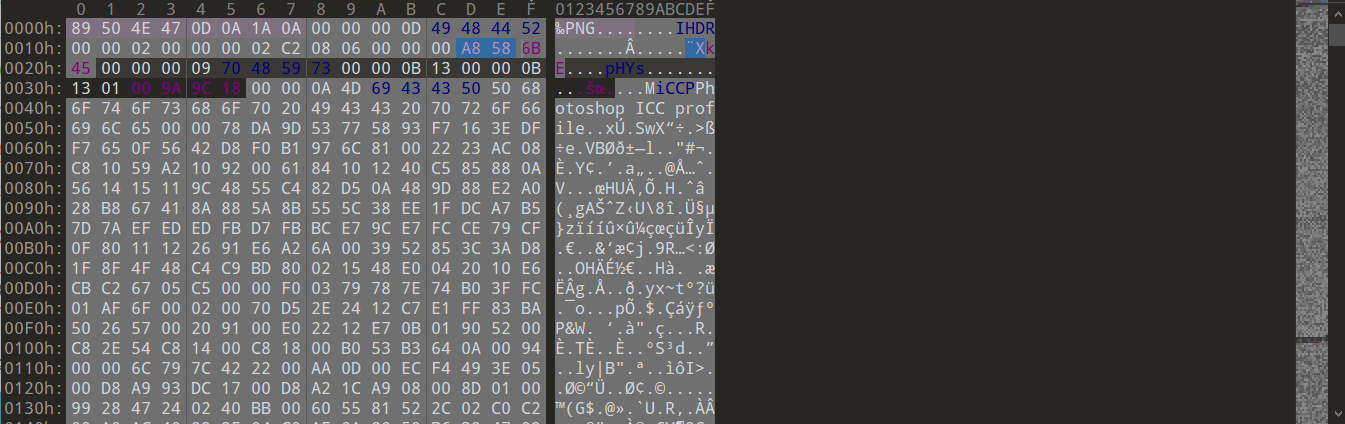
直接“顺序”写CRC
89 50 4E 47 0D 0A 1A 0APNG文件头
00 00 00 0DIDCH文件头数据块
49 48 44 52IHDR文件头数据块,固定为IHDR字符
接下来四字为宽度,如上图中00 00 02 00,以像素为单位
接下来四字为高度,如上图中00 00 02 C2,以像素为单位
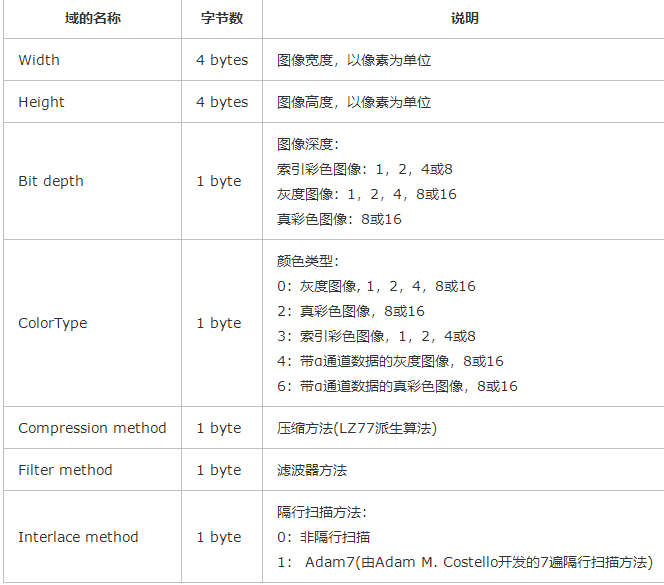
接下来五字节依次表示:
图像深度,如上图中08
颜色类型,如上图中06
压缩方法,如上图中00
滤波器方法,如上图中00
隔行扫描方法,如上图中00
接下来的四字为CRC32校验码,如上图中A8 58 6B 45
参考文献(选自):PNG文件格式具体解释 - mengfanrong - 博客园 (cnblogs.com)
ANSI escape code
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
| FILE = open("flag", 'wb')
def writeThings(b):
FILE.write(b)
def MoveLeft(n=1):
writeThings(b'\x1b[C' * n)
def MoveRight(n=1):
writeThings(b'\x1b[D' * n)
FLAG = b' 12312344444444'
import random
COUNT = 2022234
randpos = [random.randint(0, len(FLAG) - 1) for _ in range(COUNT)]
randchar = [random.randint(0x20, 0x7e) for _ in range(COUNT)]
for i in range(len(FLAG)):
pos = COUNT
for j in range(COUNT - 1, 0, -1):
if (randpos[j] == i):
pos = j
break
randchar[pos] = FLAG[i]
writeThings(b'\n')
POS = 0
for i in range(COUNT):
if (randpos[i] > POS):
MoveLeft(randpos[i] - POS)
elif (randpos[i] < POS):
MoveRight(POS - randpos[i])
writeThings(bytearray([randchar[i]]))
POS = randpos[i] + 1
writeThings(b'\n')
|
ANSI escape code 控制光标移动输出随机字符,输出量足够多然后找到flag
cmd type flag // Terminal cat flag // Powershell cat flag type flag // type效率很低,很慢
已知(e, n, c)的RSA
1
2
3
4
5
6
7
8
9
10
11
12
| import gmpy2
import binascii
c=110674792674017748243232351185896019660434718342001686906527789876264976328686134101972125493938434992787002915562500475480693297360867681000092725583284616353543422388489208114545007138606543678040798651836027433383282177081034151589935024292017207209056829250152219183518400364871109559825679273502274955582
n=135127138348299757374196447062640858416920350098320099993115949719051354213545596643216739555453946196078110834726375475981791223069451364024181952818056802089567064926510294124594174478123216516600368334763849206942942824711531334239106807454086389211139153023662266125937481669520771879355089997671125020789
e=65537
p = 11239134987804993586763559028187245057652550219515201768644770733869088185320740938450178816138394844329723311433549899499795775655921261664087997097294813
q = 12022912661420941592569751731802639375088427463430162252113082619617837010913002515450223656942836378041122163833359097910935638423464006252814266959128953
phi = (p-1)*(q-1)
d = gmpy2.invert(e,phi)
m = gmpy2.powmod(c,d,n)
print(binascii.unhexlify(hex(m)[2:]))
|
p,q在factordb.com进行质因数分解

